What’s it like to get DDoS’d
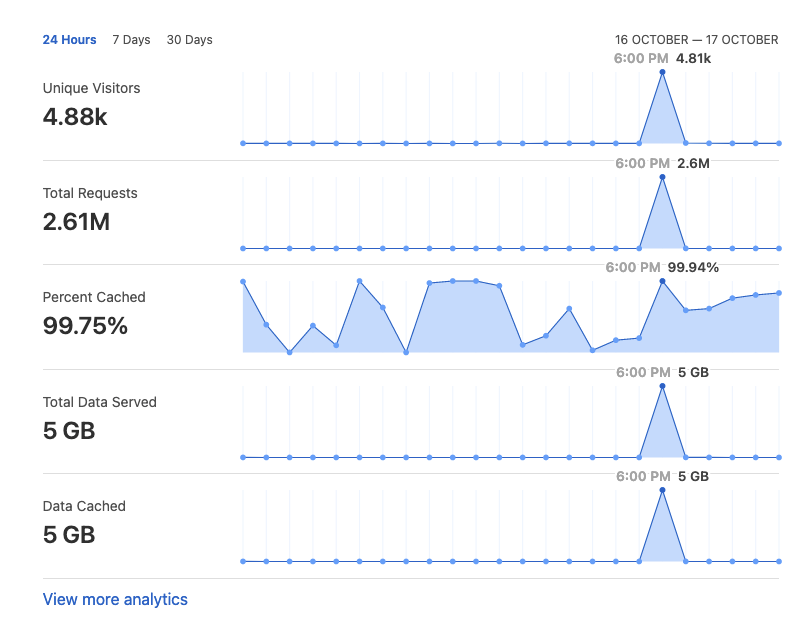
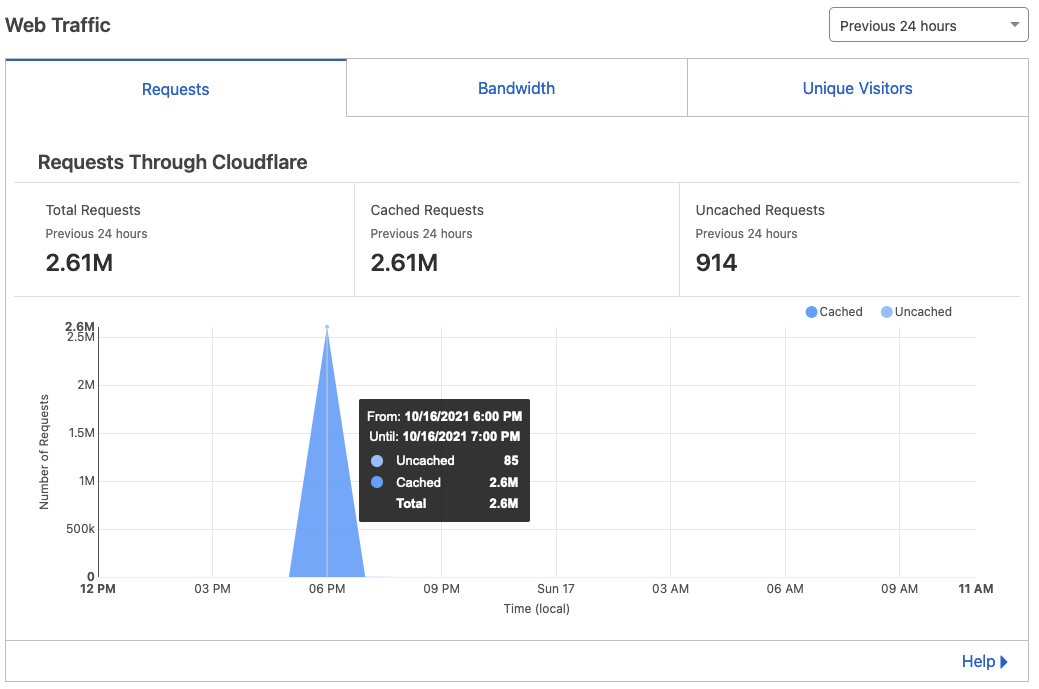
My previous post has generated certain traffic but last Saturday was different — the blog experienced an unprecedented traffic surge. “This blue cone was a DDoS” I said to myself looking at the dashboard.
Clearly, ~4.8K legitimate users cannot generate 5GB of egress traffic in a short timeframe like this.
Normally, the Firewall Event section is crystal clear, but this time it had hundreds of thousands of events.
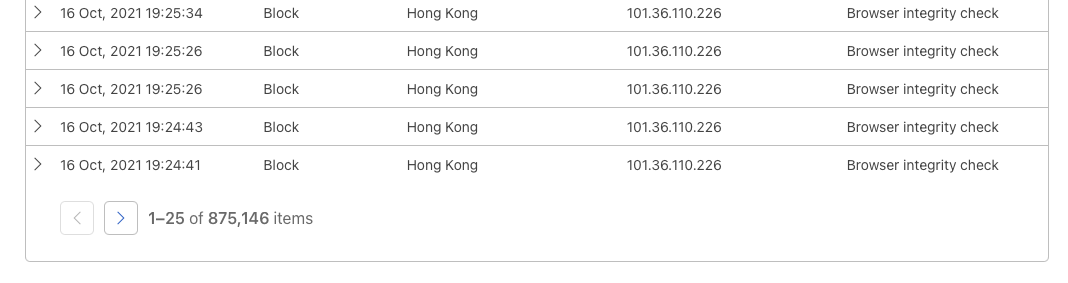
Unfortunately I wasn’t able to pinpoint the exact attack start time, because it’s impossible to jump to the last page on a free plan in a single click.
Narrowing the nature of Events shows that a bigger share of compromised traffic was recognized as HTTP DDoS.
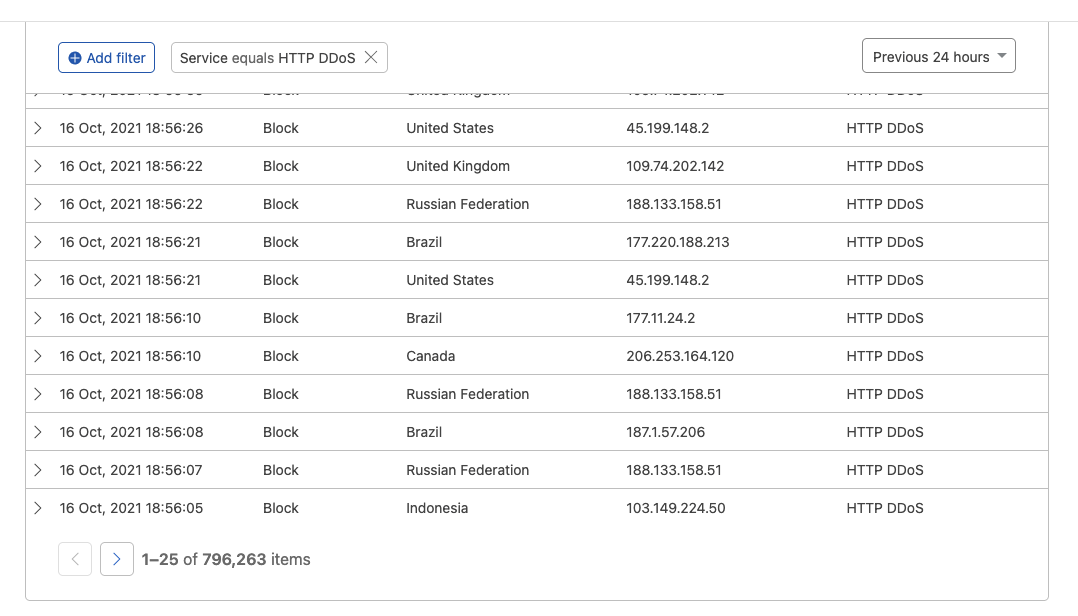
A quick peek at a wide range of traffic origins is sufficient to conclude it’s a small botnet.
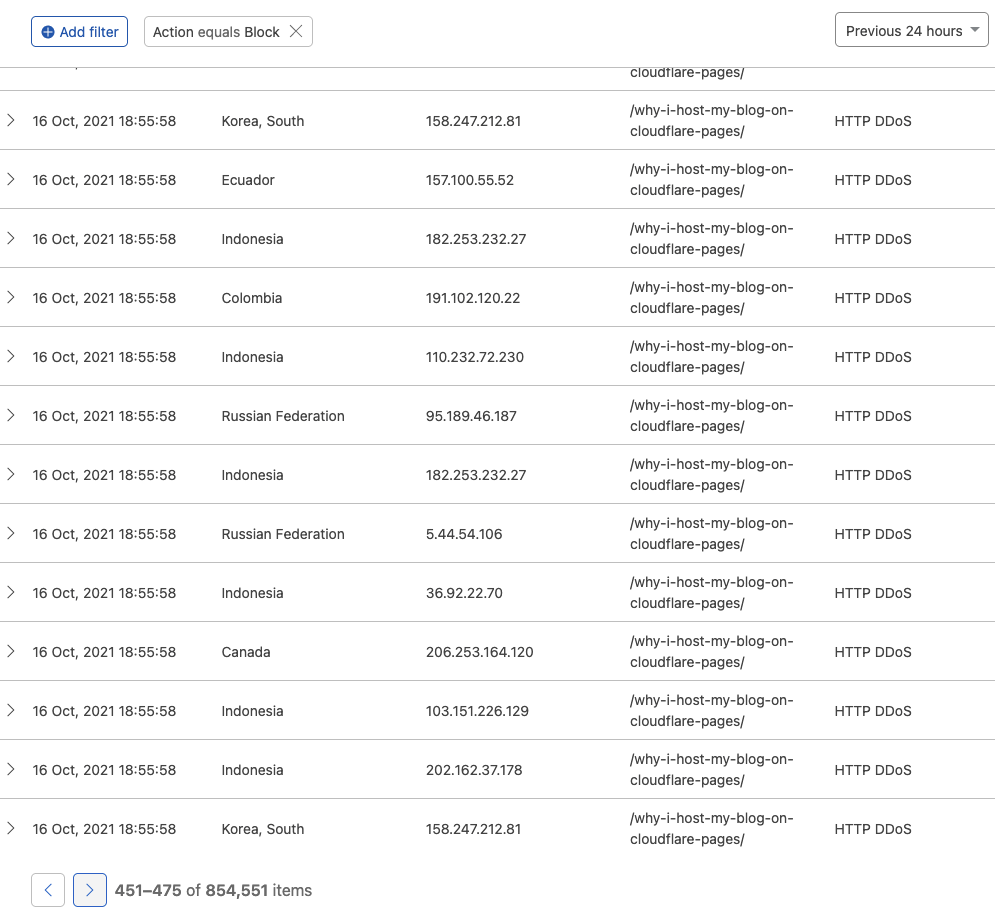
Further investigation shows that before the traffic got marked as DDoS and blocked, Cloudflare was serving an average of 720 rps from cache. Edge cache network took the HIT (pun intended).
Luckily, the attack was identified and stopped automatically thanks to DDoS Protection1 that is on by default. At this point, I can only imagine the ramifications of having a resource without any decent DDoS filtering. Perhaps, this learning experience adds yet one more reason to benefit from Cloudflare.